The rising growth of technology in Malaysia has brought along cybersecurity threats that have kept on increasing with each passing day. Malaysia has gone through so much trouble in terms of cybersecurity that this concern has surpassed the concern of physical threats. Malaysians are now quite skeptical about sharing their personal information through the mediums of the internet.
Accenture Malaysia conducted a survey in which it was highlighted that around 40% of security breaches are indirect. Such breaches take place due to weak links in the supply chain and in the overall business world.
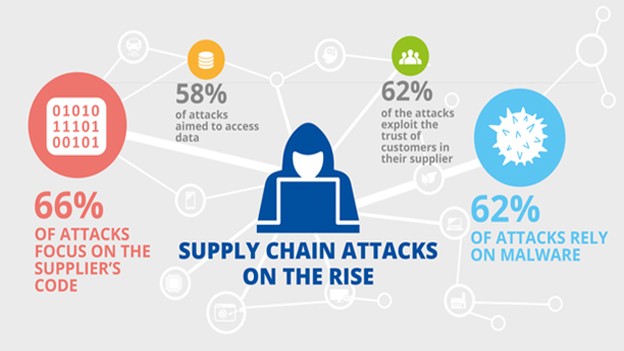
The main problem regarding supply chain attacks is that they are often overlooked. However, if enough time is given to the hackers, there could be massive destruction. Such attacks target vendors and suppliers instead of targeting the whole business.
Therefore, it becomes quite hard to detect and eliminate such attacks, especially when the vendors or the suppliers have not adopted promising cybersecurity practices, completely annulling the use of modern tools to fight cyber-attacks.
One of the examples of a supply chain cyber attack is the SITA data breach in which more than 580,000 records were exposed from Malaysia Airlines’ Frequent Flyer program. Finnair, Air New Zealand, and many other airlines reported similar attacks, exposing a large number of records of the consumers.
Singapore Airlines shared data with a company known as Star Alliance. It was the place from where the cyber-attack on the supply chain originated, making the entire supply chain vulnerable.
There are a number of similar supply chain cyber-attacks that have wreaked havoc on businesses.
What is a Supply Chain Cyber-Attack?
There are quite a few names of a supply chain attack such as a third-party attack, value-chain attack, or backdoor breach. Having said that, a supply chain attack is when an attacker is able to access a certain business through indirect channels such as vendors or suppliers or the supply chain.
Sometimes, supply chains could be quite huge. Therefore, it becomes difficult to trace the attackers.
In the past, an unsecured supplier or the vendor in a supply chain was the main culprit that was the reason for the initiation of a supply chain cyber-attack. Nonetheless, today, software supply chain cyber-attacks pose the greatest concern. The software supply chains are quite susceptible to attacks because modern software is not written from scratch.
Instead, open-source code or third-party APIs are taken into account in order to save time. But it can prove to be very dangerous for an entire supply chain.
Today, a single software project consists of around 203 dependencies. So, if any of the apps consist of even one of the compromised dependencies, then any business who would download the app from that vendor will be exposed to a cyber-attack. Hence, the number of victims grows like this!
Moreover, the software is reused. Therefore, the vulnerability would exist till the lifecycle of the software.
How Do You Detect and Stop a Supply Chain Cyber-Attack?
In December 2021, a total of 10,016 cases of cyber-attacks were reported to Cyber999. Cyber999 is a cyber security incident response center that is operated by MyCERT (Malaysia Computer Emergency Response Team). According to another study, it was highlighted that Malaysia could lose around RM51 billion from 2020-to 2024 due to cybersecurity threats. Such a huge figure makes up around 4% of the total GDP of Malaysia.
It is actually quite concerning to witness cyber-attackers spread everywhere, especially within businesses.
Ubaid Mustafa Qadri, Head of Technology Risk & Cyber Security at KPMG in Malaysia said that persistent threats, ransomware attacks, supply chain cyber-attacks, or anything new can come in with which one could struggle to emerge. So, lack of foresightedness and being reactive to the cyber-threat is actually way more dangerous than the actual threat.

Thus, it is important to have a plan ready so that it could be tested against a variety of scenarios in order to understand the impact of the attack on your business.
Having said that, let’s understand how to detect and stop the supply chain cyber-attack through a few handy measures. Here we go!
- Consider Speed as the Primary Factor
Speed matters! It does matter a lot! If the speed is enough to anticipate, detect, and stop the supply chain cyber-attack then no one can stop you from becoming the best in business in the whole globe!
Speed is that X-factor that separates your business from other players in the game. While a few of the supply chain cybersecurity policies term strength as the major factor, the majority of the practices would always put speed on number one. According to Accenture Malaysia, the cybersecurity leaders take around 15 days or less in order to identify and plug the security breaches.
Visibility, focus, and agility are the main indicators of rapid threat detection.
Moreover, through these indicators, both the buyers and the vendors can measure their abilities in a good manner.
The approach should always be proactive rather than reactive so that vulnerabilities are identified and eliminated thereby. While businesses that rely on a reactive approach are fairly slow and ineffective.
- Put Focus on Value
Now, Malaysian businesses are quite scared of cybersecurity threats. However, they should be smart enough to find out the value of money. Rather than investing with close eyes. When businesses make cyber investments without thinking twice, they automatically increase their hopes and are left shattered.
Hiscox indicated that businesses around the world have witnessed an increase in cyber security spending of 39% between 2019 and 2020.
With investments increasing rapidly, the businesses need to ensure whether their spent money was worth it or not.
Accenture Malaysia reported that 69% of the businesses feel that the growth in costs would be unsustainable in the long term. Achieving targeted results is more vital than investing money here and there.
The task should be to create effective tools that are able to identify the vulnerabilities in prior throughout the entire supply chain so that applicable measures are taken to safeguard the supply chain.
- Set a Momentum
When everything goes right, there is always a desire to add more and more tools to the arsenal. Nonetheless, the leading organizations always focus on maintaining momentum. They do not tend to go with the flow. Instead, they focus on their budget to make sure that they are aligned with it.
It is the art of doing the basics right when the time is right! The supply chain cyber-attacks have become more sophisticated. Therefore, the need of the hour is to understand the fundamentals because solutions always lie within the fundamentals, for example, securing the customer database.
It is very important to address the consequences of cybersecurity within the supply chain. If you ignore them, you are likely to come across prolonged damage. Moreover, if a supply chain data breach is ignored, your business would lose a huge amount of money.
- Get in touch with the Suppliers within the Supply Chain
Within the supply chain, the main entity is the supplier. So, working in coordination with the supplier at key levels would make sure to achieve the goals without any major hiccups. Coming across anyone who produces, manufactures, organizes, or supplies the goods is a vital step in getting to know more about the supply chain.
Businesses in Malaysia are ensuring to meet the suppliers physically. Hence, the auditing has been quite strict so that the suppliers are taking quality measures in terms of cybersecurity to prevent any minor or major cyber-attacks.
Businesses in Malaysia are in constant talks with the suppliers to demonstrate the results themselves.
Sometimes, even supply chains are not obvious. If your HVAC system consists of embedded IoT devices, then the vendor would have been refreshing the firmware on a regular basis. So, the vendor and the refreshes also become a part of your supply chain, even if you don’t consider it that way!
- Make it a Priority to Identify Vulnerabilities
The priority should be to identify the vulnerabilities within a supply chain. The first and foremost task is to identify and then eliminate immediately without wasting any more time. Make sure that you have a separate staff to look over the supply chain every once in a while.
The staff must be funded and trained specifically to eliminate the vulnerabilities right when they are in their infancy. Otherwise, delaying cyber-attacks could prove to be worse than anything!
Today, cybersecurity is a very important domain that can’t be overlooked in any case. So, make sure to prioritize where it is necessary and give your due time and effort.
The Bottom Line
In the end, it is important to note that Malaysia is growing immensely in digitizing businesses, all thanks to the pandemic. However, with the growth in the digital economy of the country, the focus should be on securing the supply chain in the best manner possible. The business owners in Malaysia should take active measures to learn about cybersecurity challenges and make it their habit to control the system in an optimal manner.